
ScubaGear is an assessment tool that verifies that a Microsoft 365 (M365) tenant’s configuration conforms to the policies described in the Secure Cloud Business Applications (SCuBA) Secure Configuration Baseline documents.
[!NOTE] This documentation can be read using GitHub Pages.
Target Audience
ScubaGear is for M365 administrators who want to assess their tenant environments against CISA Secure Configuration Baselines.
Overview
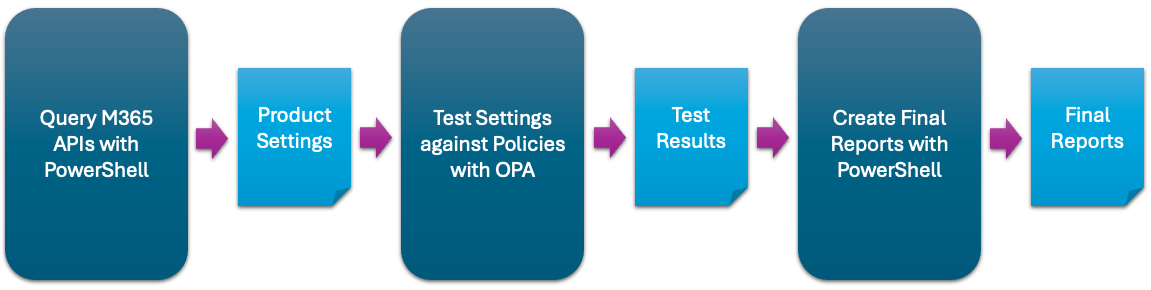
ScubaGear uses a three-step process:
- Step One - PowerShell code queries M365 APIs for various configuration settings.
- Step Two - It then calls Open Policy Agent (OPA) to compare these settings against Rego security policies written per the baseline documents.
- Step Three - Finally, it reports the results of the comparison as HTML, JSON, and CSV.
Key Features
Baseline Security Coverage
SCuBA controls have been mapped to both NIST SP 800-53 and the MITRE ATT&CK framework.
- Baselines
- Microsoft Entra ID: Identity and access management policies
- Defender: Advanced threat protection settings
- Exchange Online: Email security and compliance configurations
- Power BI: Cloud-based data visualization tool security settings
- Power Platform: Low-code application security settings
- SharePoint: Document collaboration and access controls
- Teams: Communication and meeting security policies
- Removed Policies
Scuba Configuration UI
SCuBA now includes a graphical user interface that makes it easier than ever to create and manage your YAML configuration files. This intuitive tool helps reduce the complexity of manual editing and streamlines the configuration process for your organization. For more information review the Configuration UI documentation.
UI Key Features:
- Launch with
Start-ScubaConfigApp - Step-by-step setup wizard covering all configuration options
- Real-time validation with live YAML preview
- Microsoft Graph integration for user and group selection
- Seamless import/export of existing configuration files
Ideal for users who prefer a visual interface over command-line tools.
ScubaGear Output
- HTML Reports: Interactive, user-friendly compliance reports. Sample BaselineReports.html
- JSON Output: Structured results for reporting and parsing. Sample ScubaResults.json
- CSV Export: Spreadsheet-compatible data for analysis. Sample ScubaResults.csv
Getting Started
Before launching ScubaGear, it’s important to ensure your environment is properly configured. This includes having the necessary dependencies and permissions in place.
Please review the prerequisites section to verify that your system meets all requirements. This will help avoid errors during execution and ensure a smooth experience when using ScubaGear.
[!NOTE] After installing ScubaGear in your environment, we recommend using the built-in update functions and features when you need to update to the latest version. See the Update Guide for more information.
Quick Start Guide
ScubaGear can be run multiple times to properly evaluate baseline settings.
-
First Run (No Configuration File): Start ScubaGear without a configuration file. This initial run generates a baseline template of your environment’s current settings. It does not make changes but helps you understand the default posture.
-
Subsequent Runs (With Configuration File): After reviewing and editing the generated configuration file, run ScubaGear again with the configuration file as input. This allows ScubaGear to compare your intended settings against the actual environment and elevate discrepancies accordingly.
[!IMPORTANT] ScubaGear has specific prerequisites and relies on defined configuration values to properly evaluate your Microsoft 365 tenant. After your initial assessment run, review the results thoroughly. Address any identified gaps by updating your tenant configuration or documenting risk acceptances in a YAML configuration file using exclusions, annotations, or omissions. Refer to the sections below for detailed guidance.
This iterative approach ensures ScubaGear is aligned with your environment and that all policy evaluations are based on your customized baseline.
1. Install ScubaGear
To install ScubaGear from PSGallery, open a PowerShell 5 terminal on a Windows computer and install the module:
# Install ScubaGear
Install-Module -Name ScubaGear
2. Install Dependencies
# Install the minimum required dependencies
Initialize-SCuBA
3. Verify Installation
# Check the version
Invoke-SCuBA -Version
4. Run Your First Assessment
# Assess all products (basic command)
Invoke-SCuBA -ProductNames *
5. Build YAML configuration file
ScubaGear uses a YAML configuration file to define how your environment should be evaluated. This file serves several important purposes:
- Customization – Specify which products, baselines, and rules apply to your environment.
- Configuration Mapping – Align ScubaGear’s policies with your tenant’s current settings.
- Risk Acceptance – Document intentional deviations from baselines using exclusions, annotations, or omissions.
- Traceability – Maintain a clear record of accepted risks and policy decisions for audits or internal reviews.
- Repeatability – Run consistent assessments over time or across environments using the same configuration.
[!IMPORTANT] Without a properly defined YAML file, ScubaGear will assume a default configuration that may not reflect your organization’s actual policies or risk posture. It is required if the usage is for CISA’s Binding Operational Directive (BOD) 25-01
Reuse provided sample files
[!TIP] full_config.yaml is included to help you get started. This file should be customized to reflect your tenant’s unique configuration before using it with the ScubaGear module.
6. Run ScubaGear with a configuration File
When running Invoke-SCuBA for BOD 25-01 submissions:
# Run with a configuration file
Invoke-SCuBA -ConfigFilePath "path/to/your/config.yaml" -Organization 'example.onmicrosoft.com'
For all other instances:
# Run with a configuration file (no-BOD)
Invoke-SCuBA -ConfigFilePath "path/to/your/config.yaml" -SilenceBODWarnings
7. Update ScubaGear
The following will update ScubaGear.
# The following will update ScubaGear to the latest version
Update-ScubaGear
The following will baseline all ScubaGear dependencies, please review the Update Guide in detail before running.
# The follwing will remove and re-install all ScubaGear dependencies
Reset-ScubaGearDependencies
Table of Contents
Getting Started
Installation
#### Prerequisites
Configuration & Usage
- Configuration UI - Graphical interface
- Configuration File - YAML-based configuration
- Parameters Reference - Command-line options
Running Assessments
Troubleshooting & Support
Automation
- ScubaConnect - ScubaConnect is cloud-native infrastructure, developed by CISA, that automates the execution of assessment tools ScubaGear and ScubaGoggles.
Additional Resources
Project License
Unless otherwise noted, this project is distributed under the Creative Commons Zero license. With developer approval, contributions may be submitted with an alternate compatible license. If accepted, those contributions will be listed herein with the appropriate license.





