
A powerful, easily deployable network traffic analysis tool suite for network security monitoring
Overview
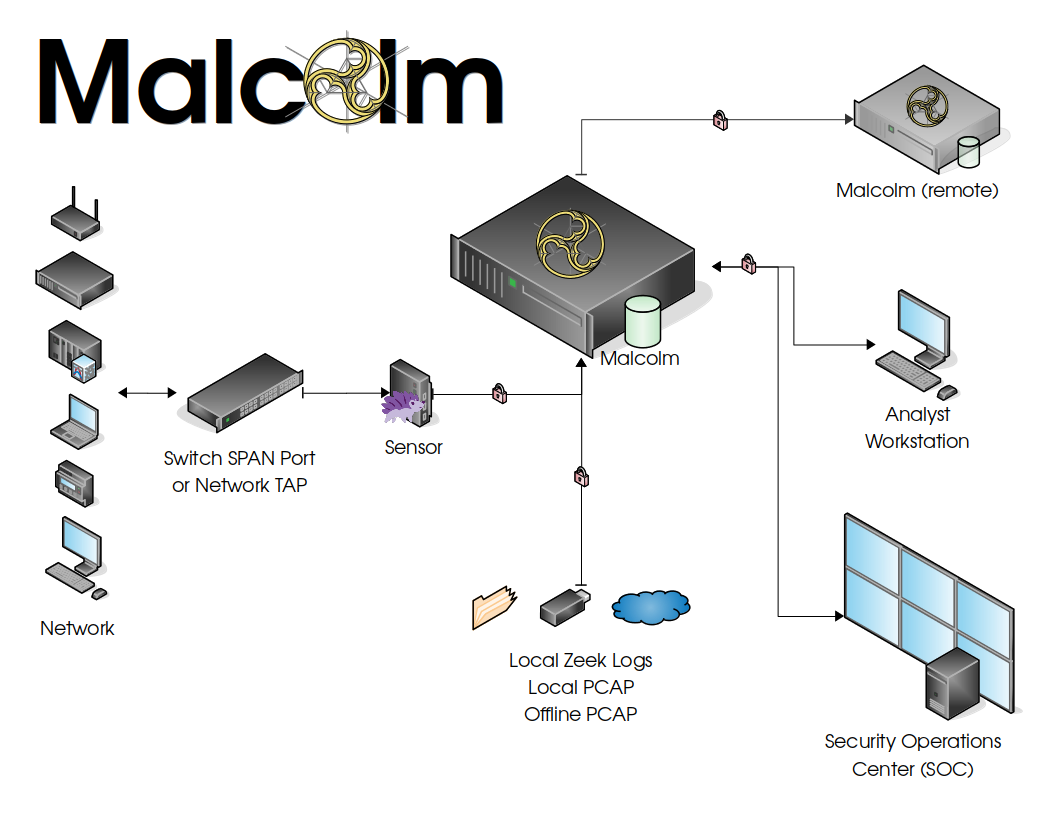
Malcolm processes network traffic data in the form of packet capture (PCAP) files or Zeek logs. A sensor monitors network traffic mirrored to it over a SPAN port on a network switch or router, or by using a network TAP device. Zeek logs and Arkime sessions are generated containing important session metadata from the traffic observed, which are then securely forwarded to a Malcolm instance. Full PCAP files are optionally stored locally on the sensor device for later examination.
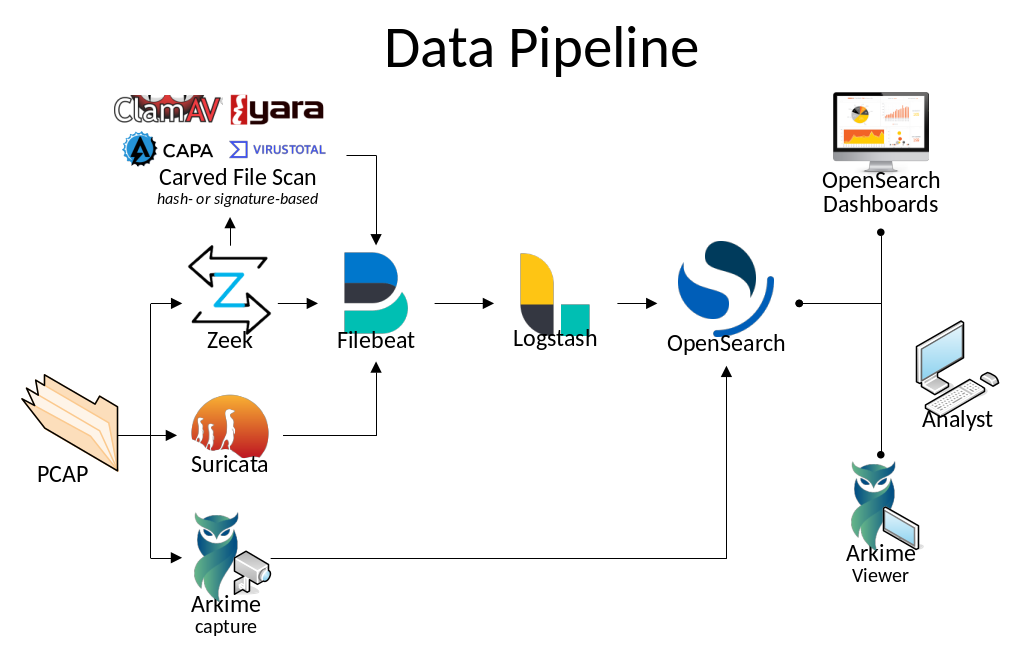
Malcolm parses the network session data and enriches it with additional lookups and mappings including GeoIP mapping, hardware manufacturer lookups from organizationally unique identifiers (docs/OUI) in MAC addresses, assigning names to network segments and hosts based on a user-defined asset inventory, performing JA4 fingerprinting, and many others.
This enriched data is stored in an OpenSearch document in a format suitable for analysis through two intuitive interfaces: OpenSearch Dashboards, a flexible data visualization plugin with dozens of prebuilt dashboards providing an at-a-glance overview of network protocols; and Arkime, a powerful tool for finding and identifying the network sessions comprising suspected security incidents. These tools can be accessed through a web browser from analyst workstations or on a display in a security operations center (SOC). Logs can also be forwarded on to another instance of Malcolm.
Malcolm can also easily be deployed locally on an ordinary consumer workstation or laptop for smaller networks, use at home, or in the field incident response engagements. Malcolm can process local artifacts such as locally generated Zeek logs, locally captured PCAP files, and PCAP files collected offline without the use of a dedicated sensor appliance.
- Quick start
- Components
- Supported Protocols
- Downloading Malcolm
- Development
- Configuration
- Running Malcolm
- Network traffic artifact upload
- Live analysis
- Arkime
- OpenSearch Dashboards
- Search Queries in Arkime and OpenSearch Dashboards
- Other Malcolm features
- Analytics
- Custom Rules, Scripts and Plugins
- Automatic file extraction and scanning
- Index management
- Event severity scoring
- Zeek Intelligence Framework
- “Best Guess” Fingerprinting for ICS Protocols
- Asset Interaction Analysis
- CyberChef
- API
- Forwarding Third-Party Logs to Malcolm
- Malcolm installer ISO
- Deploying Malcolm with Kubernetes
- Deploying Malcolm on Amazon Web Services (AWS)
- Hardening
- Installation example using Ubuntu 24.04 LTS
- Hedgehog Linux - Malcolm’s Network Sensor
- End-to-end Malcolm and Hedgehog Linux ISO Installation
- Upgrading Malcolm
- Modifying or Contributing to Malcolm